Using Nmap on Windows | HackerTarget.com

Running Nmap on Windows is not as difficult or problematic as it was in the past. Nmap is supported on Windows 7 and higher with performance close to if not quite as good as Linux based operating systems. The majority of users still do use *nix based systems however a good number of people use it on Windows.
By installing Nmap on your Windows based systems you have access to
the world's best port scanner for security testing and troubleshooting
of network connectivity. In addition you have ncat available a full-featured version of netcat a virtual swiss army knife for networks. I am a big fan of ncat and encourage any system administrator or techie to explore the options.
Installing Nmap for Windows
To install the Windows version of Nmap download the executable installer and click through the wizard. It is your standard Next | Next | Next | finish... all done. By default, the Nmap installation directory will be added to the system path. With Nmap in your system path, you can run nmap or ncat from any command window.
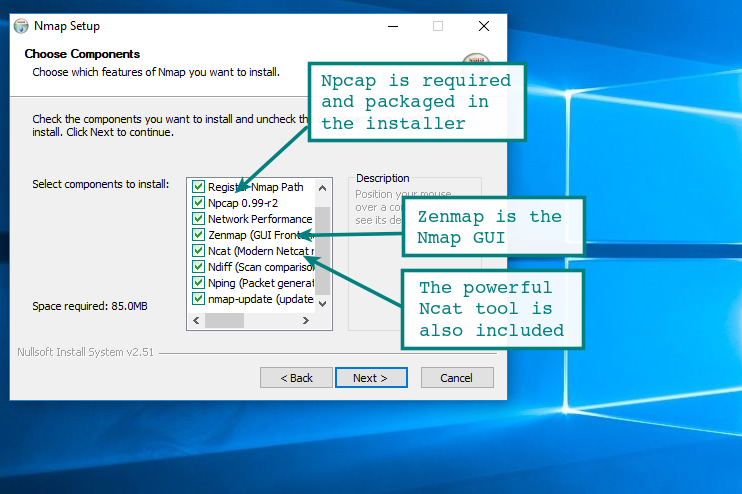
It will run on all the more modern versions of Windows including Windows 7, 2008 and Windows 10. If you are running something older such as 2K or earlier you may run into problems, but if you are still on those platforms you already have problems...
If you install from the zip file, there are a few additional configuration items to be aware of and apply. These are all documented on the nmap installation page for Windows.
 Nmap on the Windows Command Line
Nmap on the Windows Command Line
During a default installation of the Nmap Windows package, the
installation path will be added to the system path. Simply fire up a
command prompt and launch nmap. If you installed from the
standalone zip file, you need to add the installation folder to the
system path manually through system properties.
As you can see the familiar Nmap command options appear after running the command. Access to the Nmap NSE scripts is available as are all the standard options.
Zenmap on Windows
Zenmap is an excellent GUI front-end to the Nmap core scanning engine. It has some pretty nifty features that are not available with the command line version, in particular the network topology map. This rivals commercial mapping tools that perform a similar function and is a nice feature.
It is also intuitive to browse through results from different hosts using Zenmap, there are options to save the results in standard Nmap format (.nmap) or as XML (.xml) for further processing. There does not appear to be the option to save in the standard Grep format (-oG).
Zenmap is available on Windows and Linux distributions, it can be a great introduction for those less familiar with the command line.
Testing SMB Security with Nmap NSE Scripts
Bundled with Nmap are addon scripts that perform all manner of functionality. Of note to those in a Windows environment are the 34 smb-
scripts that are available. These allow enumeration of entities on
Windows systems remotely using the Microsoft SMB protocol (port 445).
Examples include smb-os-discovery, smb-enum-users and smb-brute.
There are also vulnerability detection scripts, for testing even the most recent high profile Windows vulnerabilities. Head over to the Nmap NSE scripts page for all the documentation and a list of the scripts.
| smb-vuln-ms08-067 | Test Microsoft Windows systems for the very popular remote code execution vulnerability known as MS08-067. For years this was the go to exploit when using Metasploit. Note this check is dangerous and it may crash systems. |
| smb-vuln-ms10-054 | Detect whether target machines are vulnerable to ms10-054 the SMB remote memory corruption vulnerability. |
| smb-vuln-ms10-061 | Attempts to discover whether systems are vulnerable to ms10-061 Printer Spooler vulnerability. |
| smb-vuln-ms17-010 | Attempts to detect if a Microsoft SMBv1 server is vulnerable to a remote code execution vulnerability ms17-010. The vulnerability is actively exploited by WannaCry and Petya ransomware and other malware. |
Wrapping Up
Having access to both Nmap and ncat when on a Windows system is very convenient and lots of fun. There is an amazing number of tricks that can be done with ncat, whether you are troubleshooting, security testing or just need some network-fu during a penetration test.
There are now 600 Nmap NSE scripts. The capabilities these provide is another bonus for having Nmap installed on your Windows workstation. Using the bundled scripts there are large number of short cuts and tests that can be conducted that might otherwise be difficult without additional software installed.
Thanks for reading, we also have a tutorial and cheat sheet for those wanting to discover more about this excellent tool.
Know Your Perimeter
Trusted tools. Hosted to save you time.
Comments
Post a Comment